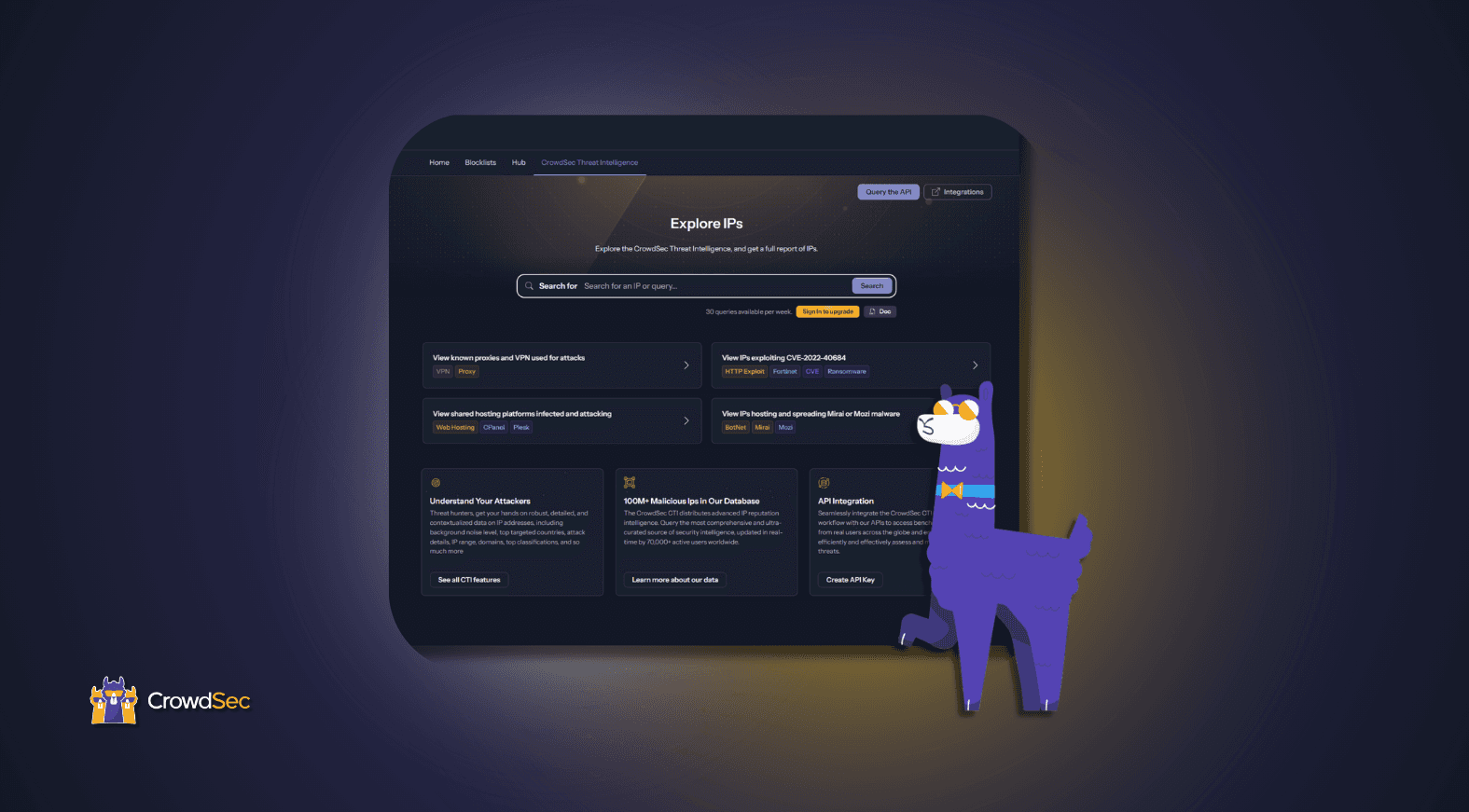
The highly requested Community API Key is now available for all those who wish to try our CTI data outside of the CrowdSec Console. You can now query our global CTI database with other tools such as SEKOIA.IO, TheHive, MISP, OpenCTI, and many more (see full list at the bottom of article + link to documentation on each of them as well as the integrations coming soon)!
What does the Community API Key allow you to do?
With the community key, you’ll be able to request information up to 50 times a day on this endpoint: https://cti.api.crowdsec.net/v2/smoke/{ip}.
For example, our friends over at SEKOIA.IO have created a playbook with the possibility to add CrowdSec’s CTI to enrich your alerts and gather more information on the IPs attacking your systems. We have also worked on creating integrations for other platforms such as TheHive, MISP, and OpenCTI. You can read all the details about those integrations here.
The type of data you can get from CrowdSec cyber threat intelligence are:
- IP & IPrange
- Autonomous System
- Country of origin
- First and last sighting
- Classification & attacks its known for
- Top targeted countries
- Aggressiveness overall
How to begin using the Community API Key?
From your free CrowdSec Console account you can generate an API within the settings panel (API documentation here).
List of our current and upcoming CTI integrations
- MISP
- OpenCTI
- TheHive – Cortext Analyzer
- PaloAlto Cortex XSOAR
- Maltego Transforms
- SEKOIA.IO
- Splunk SOAR
✨ Coming soon
- DataDog
- QRadar
- Splunk SIEM
…And many more: feel free to get in touch with us via Discord to share your use cases and collaborate on integrating CrowdSec in your tools of choice!