
Welcome to the CrowdSec Blog
Learn more about CrowdSec, our approach to tactical intelligence, and company news.
AnnouncementInside CrowdSecProactive CybersecurityGuest PostData CurationAmbassador PostIntegrationsPartnersCrowdSecEvents


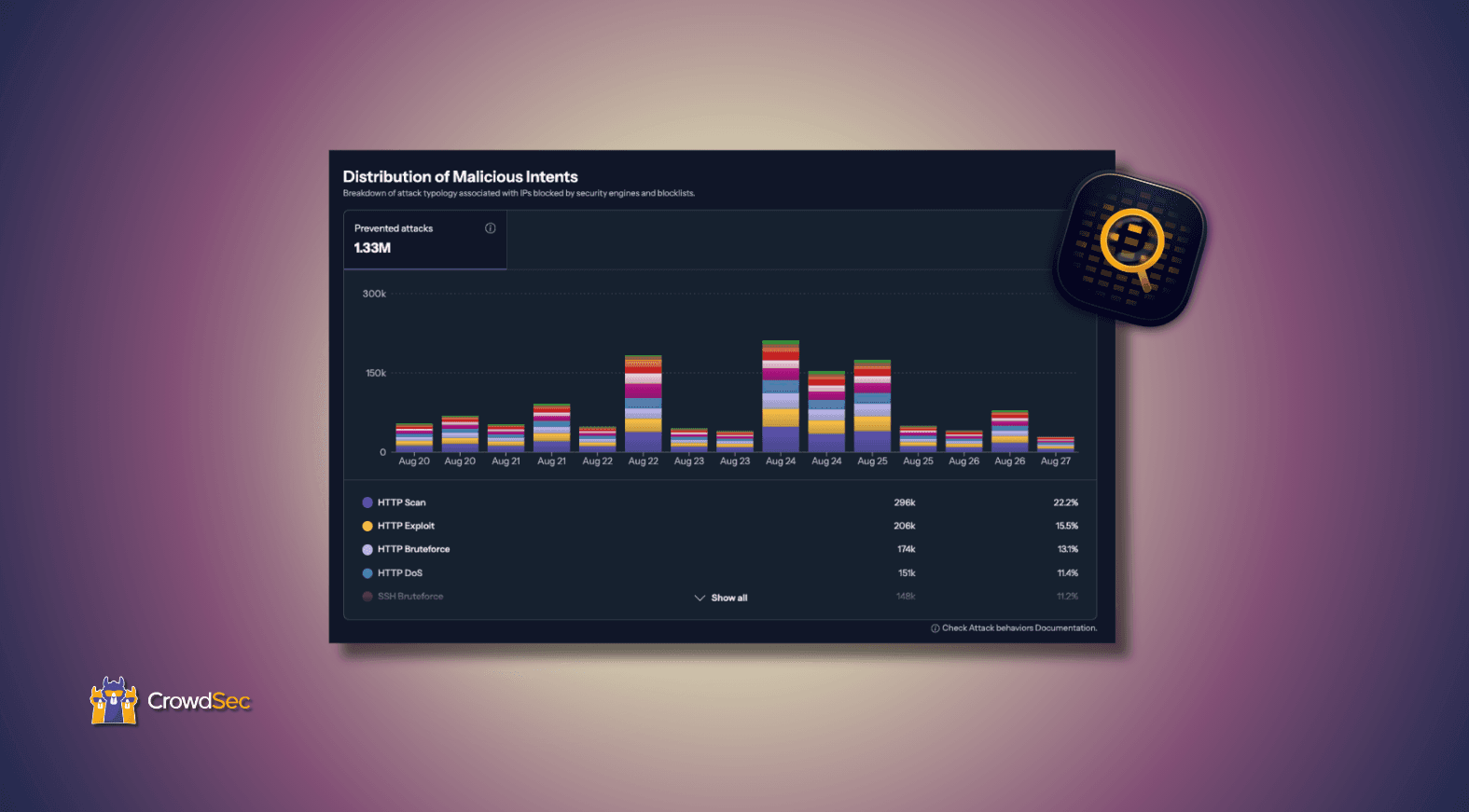
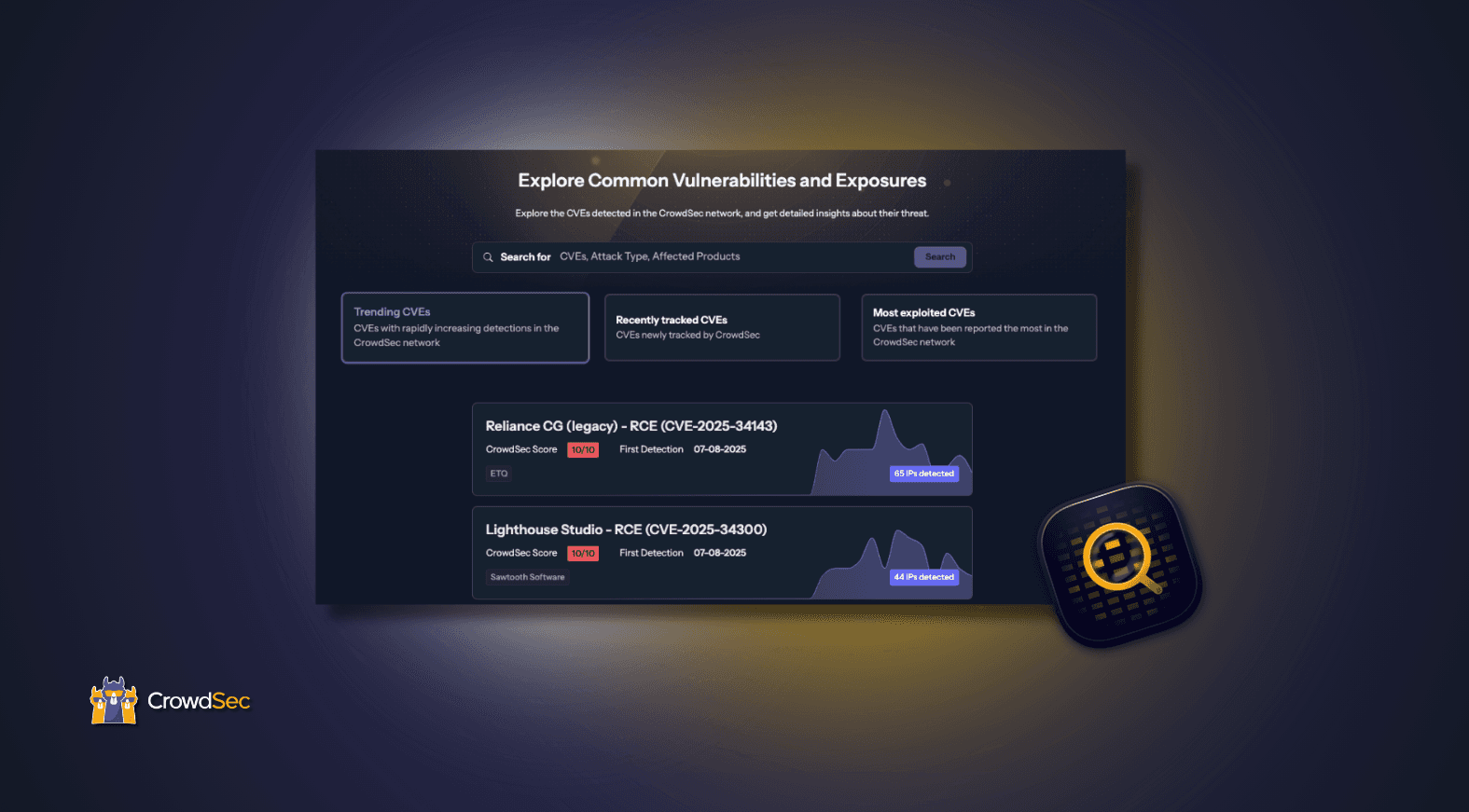
Check out our VulnTracking Reports!
View VulnTracking Reports

Announcement
Protecting CAPI reliability: Introducing rate limiting on CrowdSec’s Central API
To keep CrowdSec’s Central API (CAPI) reliable as usage continues to grow, we’ve introduced rate limiting. This change helps prevent misconfigured or broken deployments from generating excessive traffic, ensuring fair access and consistent performance for everyone.











Check out our VulnTracking Reports!
View VulnTracking Reports



Announcement
Protecting CAPI reliability: Introducing rate limiting on CrowdSec’s Central API
To keep CrowdSec’s Central API (CAPI) reliable as usage continues to grow, we’ve introduced rate limiting. This change helps prevent misconfigured or broken deployments from generating excessive traffic, ensuring fair access and consistent performance for everyone.














